In the past few blogs (All Roads Lead to Kubernetes, and Deceiving Attackers in a Kubernetes World) we zeroed in on the cloud native environments being the next frontier for the attacker-defender games. We also commented on how deploying deception in a Kubernetes-based environment is an easy approach to detecting attackers that have breached into the infrastructure. Still, deriving the right stack of deception workload to deploy can be tricky. Let’s dig into how to deploy an effective decoy in cloud environments.
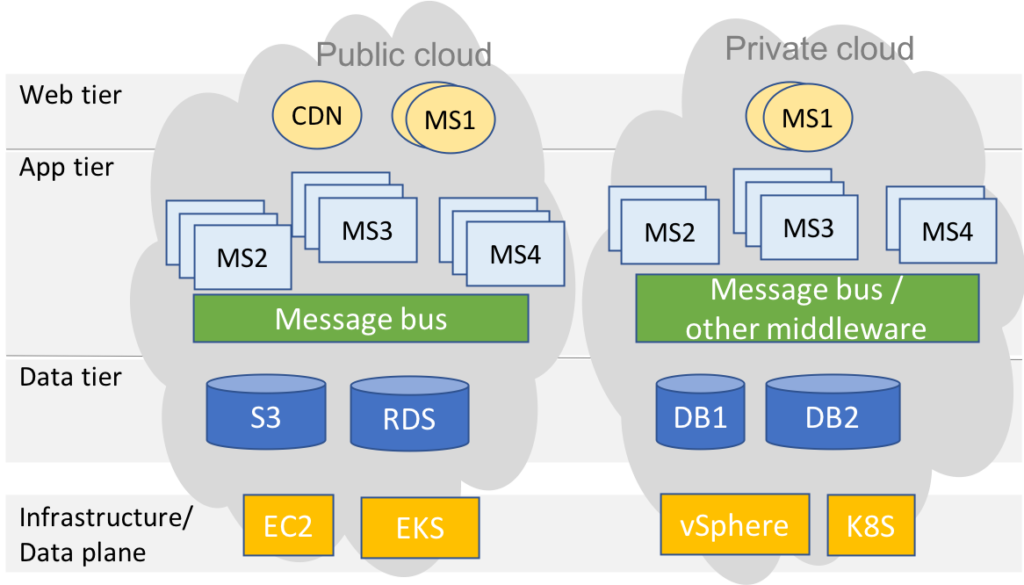
Ideally, the deception should mirror the application. The next generation of applications are designed with scale and agility as their top goals. This requirement means they typically span the hybrid cloud, are based on a microservices design pattern, and leverage as many native cloud services (e.g., AWS S3, Spark/EMR) as your budget would allow. The figure below illustrates a typical application stack. This expanded set of options to build applications increases the attack surface and makes it essential that any security solution cover all these diverse resources at cloud scale. Consequently, the deception objective is to mimic production applications and spin up decoys as a tiered-stack that includes front-end, message bus, database and backend tier services, without conflicting or overlapping with existing production workloads, that will work across the full spectrum of platforms in the hybrid cloud.
Acalvio’s ShadowPlex Cloud does just that for you! Based on a production workload blueprint, ShadowPlex Cloud controller applies data-science based recommendation to determine the most effective rollout of decoy EC2 or other virtual machine instances, S3 buckets and SQL databases, and Kubernetes pods and services (either in existing namespaces, or a completely new decoy namespace). The inserted decoys can be customized if desired or the security operator can choose to just go with the default recommendation set. Once the decoys are deployed, the appropriate breadcrumbs will, then, be added as environment variables, registry references, and configmaps so as to lead an attacker to the decoys. This makes ShadowPlex Cloud an effective tool in cloud malware detection with negligible false positives.