BreadCrumbs and Lures are very critical components of any deception based architecture. As the name suggests, breadcrumbs and lures aid to divert a threat a threat actor (an individual or malware) to deception sensors. The moment the deception sensor gets tripped, instead of blocking the multi-stage threat, the threat actor is allowed to execute its weaponry in a monitored network. This execution of all the stages of an attack can help gather pertinent indicators of compromise that can be fed back to the inline or endpoint detection devices for timely and effective prevention. This was discussed in our previous blog looking deep into a multi-stage attack.
There are multiple ways in which breadcrumbs or lures can be projected to divert an imminent threat. This blog will discuss two approaches that can be used to project breadcrumbs. The first method is statically spraying the breadcrumbs on the host. The second manner is a dynamic approach, one where breadcrumbs are projected on the system during the execution of the malicious code.
Approach #1 – Static BreadCrumbs & Lures:
This involves spraying breadcrumbs or lures on the host, thereby leading the threat actor to deceptions. The inherent advantage is that that it does not require any agent on the host to monitor them. As an example, Figure 1.0 shows the code from ransomware which is accessing the drives on the endpoint.
GetDriveTypeW can be used to determine the drive type, following which the expression ‘result == 3’ checks if the drive is fixed, ‘result== 2’ checks if the drive is removable, and ‘result==6’ denotes if it is a RAM disk. If any of these drives are found, the routine ‘sub_402CFB’ is called, which then forks a thread to encrypt the files in these drives. The function GetDriveTypeW can also be used to access a remote mapped network drive. The value 4 being returned by the function GetDriveTypeW denotes a remote mapped drive. Encrypting mapped drives has been done extensively by ransomware. In order to detect the ransomware which can encrypt mapped drives, honey mapped drives will be projected on the endpoint as static breadcrumbs. These honey mapped drives will be accessed by ransomware, it will start to encrypt files in the honey mapped drives, and it can be detected that ransomware has compromised the endpoint.
Static breadcrumbs are agentless; they do not need any agent to monitor them on the host in which they are sprayed. However, for static bread crumbs to be effective in diverting a threat actor to a deception, it has to be ensure that the probability of accessing and using the honey breadcrumbs, is more than the legitimate data.
Approach 2# – Dynamic BreadCrumbs & Lures:
Dynamic breadcrumbs and lures are honey values that get dynamically generated by an agent on the host, during the actual execution of a malicious code path. When the agent on the infected host determines that the process is malicious, it provides honey values to the API calls made by the process, which in turn ensures that the ongoing threat gets diverted to the deceptive host.
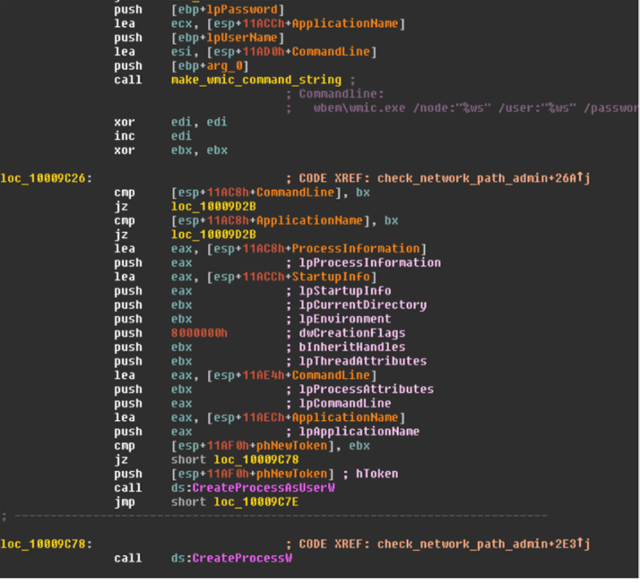
Let us use an example to explain where the dynamic breadcrumbs will get activated on the infected host to divert the threat to the deceptive host. Figure 3.0 shows code from the Petya worm. Credentials for spreading via WMI are obtained via CredEnumerate API calls (as shown in figure 3.0), which are scraped from memory. Credentials are then stored in a global object, accessed by the spreading WMI function as shown in figure 4.0.
In case of Petya, after confirming a process is malicious, honey user and passwords will be provided to the API call CredEnumerateW. Honey username and passwords will ensure that Petya can only log on to deceptive hosts on the network and the actual hosts on the networks are protected. In this case, we are assuming that Petya is executing in an environment which is patched for vulnerabilities MS17-010 and using WMI with stolen credentials for spreading.
Since dynamic breadcrumbs are provided during execution of malicious code, it is a deterministic model of diverting an attack to deceptive hosts.
Conclusion:
Since Deception-based architectures allow execution of every stage of a multi-stage attack, it is a robust model to detect and analyze an ongoing attack. Breadcrumbs and Lures aid deception solutions to divert or lead the threat actor to deceptive hosts. In this blog, we have discussed static and dynamic breadcrumbs or lures to divert an ongoing threat to deception. Static breadcrumbs provide an inherent advantage that they do not require any monitoring whereas dynamically projected breadcrumbs provide an advantage that they will always divert a multi-stage attack to deception.


