
The Cyber Kill Chain
If you’re reading this blog, you likely know the basics of the cyber kill chain. You might even be able to name a few of the seven stages in the kill chain, which lays out the steps adversaries take to attack and exploit their victims. Where you might have a lot more difficulty is in explaining two things: how attackers actually execute these steps, and what you’re doing to detect and mitigate them.
Too much Focus on Early Steps of the Kill Chain
At Acalvio we tend to see too much focus on the early steps of the kill chain, which detail how attackers initially get in. For example, most organizations are well-aware that phishing is a big problem, and have training and technology in place to try to deal with it. However things get dicey in the later stages, which detail how attackers establish a persistent footprint, discover sensitive data targets, and exfiltrate said data. It’s true that certain limited technologies (e.g. endpoint detection) are gaining traction. But beyond that it’s not a pretty sight.
MITRE | ATT&CK
The US Government agrees that this problem is widespread, and they tasked MITRE (the non-profit that does government-sponsored research) to tackle it. As a result, MITRE has recently published what they call ATT&CK, which is dedicated to addressing how attackers execute the post-infiltration stages of the kill chain. Crucially, ATT&CK documents exactly what tactics and techniques adversaries actually use – it’s not a theoretical exercise. Want to know what methods you need to be able to detect and defend against? ATT&CK should be your first port of call.
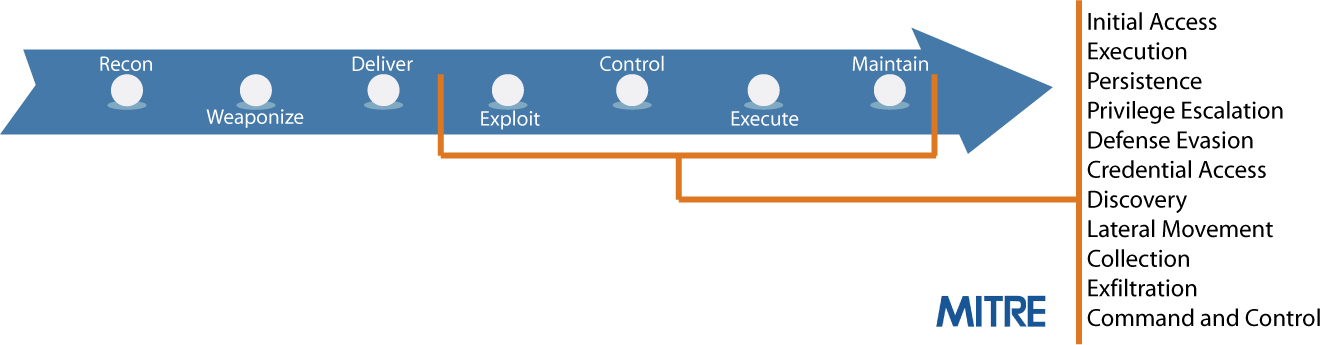
MITRE ATT&CK focuses on the kill chain’s post-infiltration stages
Acalvio ShadowPlex
Acalvio solutions were designed to handle the actual post-infiltration threats and techniques you’re likely to encounter as you try to defend your network. In fact Acalvio ShadowPlex provides capabilities relevant to 7 of the 11 tactics in the ATT&CK framework. At a high level, Acalvio delivers
- Fast and accurate incident detection
- Adversary engagement and forensics
- Threat response to retard attack propagation
Like MITRE ATT&CK, Acalvio starts with the premise that attacks will be successful in penetrating the network – we focus on “I know they’re here – what should I do about it?” ShadowPlex is designed to detect typical attacker methods quickly, so that response measures can be executed before persistence and data exfiltration is achieved. Furthermore, we facilitate slowing down the attacker and gathering information on their methods. Taken together, they go beyond pure detection, and provide significant assistance with containment and remediation efforts.
There are numerous security frameworks floating around, but none that are as tightly aligned with the post-infiltration threat landscape reality as ATT&CK. With limited budgets and staff time, you need to focus on the real threats and techniques, not the theoretical ones. Alcavio recommends MITRE ATT&CK as a great place to start. Want to know more? Know more about the full ATT&CK Technique Matrix. And detailed info on how ShadowPlex helps you get a grip the ATT&CK tactics and techniques can be found .
MITRE ATT&CK™: Design and Philosophy, July 2018



