Malicious behavior: we generally know it when we see it
Most of the time, unfortunately, malicious behavior is hidden from view. Consider that the average dwell time for cyberattackers within networks is still measured in months. Per FireEye, the global median dwell time in 2018 was 78 days, down from 101 days in 2017, but still far too long.
Malicious behavior may manifest itself as the discovery or use of software designed to gain access and to leverage or create vulnerabilities that can be used to further penetrate networks, endpoints, and servers; perform reconnaissance; gain authentication data; and ultimately exfiltrate sensitive information or damage ongoing enterprise operations. Alternatively, it may manifest itself through the more subtle activities of malicious insiders.
How can we detect malicious behavior more rapidly and reduce dwell time, thereby reducing the risk of a successful data breach?
There are several technologies in play that are used today in networks. This includes network threat detection using unsupervised machine learning, supervised machine learning, and deception technology. Deception technology also integrates machine learning where it provides an advantage to analysis and discovery.
Supervised machine learning
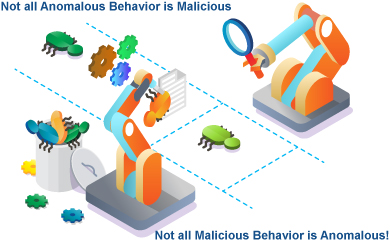
Supervised machine learning is an important technology used in cybersecurity, often for network threat detection. Algorithms such as supervised neural nets, Bayesian networks, k-nearest neighbors, and other variants are commonly used. Supervised machine learning is a type of machine learning where automation learns how to classify activity based on examples of behavior that produce a recognized output value. Supervised machine learning algorithms use training data to help establish the boundaries of classification. Inside of the boundary may be deemed as normal and hence acceptable behavior. Outside is anomalous behavior. If you pull the requirements too tightly with your training data, the amount of apparent anomalous behavior increases substantially. If you loosen the training requirements, almost nothing will appear anomalous. You can see how one moment, in one scenario, anomalous behavior which is truly valid might appear malicious, while malicious behavior might not show as anomalous at all.
Unsupervised machine learning
Unsupervised machine learning is another important technology used in cybersecurity. Algorithms commonly used for unsupervised machine learning include k-means, c-means, self-organizing maps (SOM), and one-class support vector machines. Unsupervised machine learning, simply put, doesn’t require training data. The key assumption of unsupervised machine learning is that the bulk of existing behavior is normal, which thereby segregates infrequent and statistically uncommon activity as suspect and possibly malicious. In this case, an infrequent but valid user activity may be flagged as statistically anomalous, while pre-existing network threats might inadvertently be missed when unsupervised machine learning is set-up. These undetected threats often arise in markets like health care, manufacturing, and financial and banking networks. Statistical sensitivity can be adjusted, but, in the final analysis, there must be a set boundary condition, just as there was in supervised machine learning. On one side, what appears to be non-anomalous behavior can be malicious, and vice versa.
Acalvio ShadowPlex Core Technology
Acalvio ShadowPlex core technology is not conditional, statistical, or probabilistic. The detection is absolute and 100 percent certain. We integrate machine learning but temper our use with absolute adherence to our core policy alignment: nothing, absolutely nothing, should be engaging with our decoys at any time.
As we have seen, not all malicious behavior within your networks will stand out as anomalous. In counterpoint, not all anomalous behavior within your networks is necessarily malicious.
- Deception technology focuses attention on those instances of behavior that are clearly in violation of process and immediately identifies these threats present within your network at virtually 100 percent certainty.
- Deception technology provides virtually flawless detection to ensure that threats are rapidly identified and rapidly shut down.
Please talk to us about how deception technology is an important adjunct to your other security controls! We’d be pleased to introduce you to our latest technology and share information about how Acalvio ShadowPlex protects the most sensitive enterprise and government networks.


