
The NSA, CISA, and allied cybersecurity agencies from the Five Eyes intelligence alliance, including the UK Government, Canadian Centre for Cyber Security, New Zealand National Cyber Security Centre have released comprehensive guidance to mitigate threats against Active Directory (AD), highlighting 17 common attack techniques used by adversaries. Given AD’s fundamental role in central authentication and authorization, it is an attractive target for attackers aiming to elevate privileges and gain unauthorized access to critical systems and sensitive data. The report is available at:
https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3917556/nsa-jointly-releases-guidance-for-mitigating-active-directory-compromises/
The Inherent Challenges of Active Directory Security:
“Specifically, Active Directory’s susceptibility to compromise is, in part, because every user in Active Directory has sufficient permission to enable them to both identify and exploit weaknesses. These permissions make Active Directory’s attack surface exceptionally large and difficult to defend against. Also contributing to its vulnerability is the complexity and opaqueness of relationships that exist within Active Directory between different users and systems. It is often these hidden relationships, which are overlooked by organisations, that malicious actors exploit, sometimes in trivial ways, to gain complete control over an organisation’s enterprise IT network.“
Active Directory’s (AD) architecture, designed as a central catalog, is inherently open and accessible to all domain members. This essential openness makes AD particularly vulnerable to enumeration attacks, where attackers can uncover administrative accounts and critical systems. Such reconnaissance boosts the success rate of attacks, enabling malicious actors to strategically target and compromise key organizational assets.
Attackers exploit AD’s fundamental characteristics by initially accessing any domain account, often via phishing or credential theft. Once inside, they conduct targeted enumerations to map out the network’s landscape—identifying admin accounts and key systems. If compromised, these can lead to broader network control or significant data breaches.
With attackers gaining trusted access to an endpoint and performing AD enumeration by leveraging this trust, traditional prevention-based security strategies are proving inadequate to stop the attacker. Organizations must, therefore, extend beyond prevention to strengthen their detection capabilities.
Despite efforts to harden AD environments and mitigate misconfigurations, the core architecture of AD, with its inherent openness and centrality, cannot be fundamentally altered. This immutable aspect of AD’s architecture attackers will continue to find techniques to exploit the attack surface presented by AD.
Active Directory attacks are challenging to detect
“Detecting Active Directory compromises can be difficult, time-consuming, and resource intensive, even for organisations with mature security information and event management (SIEM) and security operations centre (SOC) capabilities. This is because many Active Directory compromises exploit legitimate functionality and generate the same events that are generated by normal activity.”
The guidance outlines a variety of AD attack techniques, such as Kerberoasting, DCSync, and Silver Ticket attacks, and discusses the use of offensive tools like Mimikatz, Rubeus, and Impacket, which are commonly employed by ransomware and advanced persistent threat (APT) actors.
Traditional detection methods like log analytics and network traffic analysis often fall short because these stealthy attack techniques do not produce anomalous patterns in logs or network traffic, rendering such methods ineffective. For example, Kerberoasting attacks, which involve performing an offline brute force to crack the service ticket and obtain the clear text password for a service account, results in no detectable events or logs, making this particularly difficult to detect.
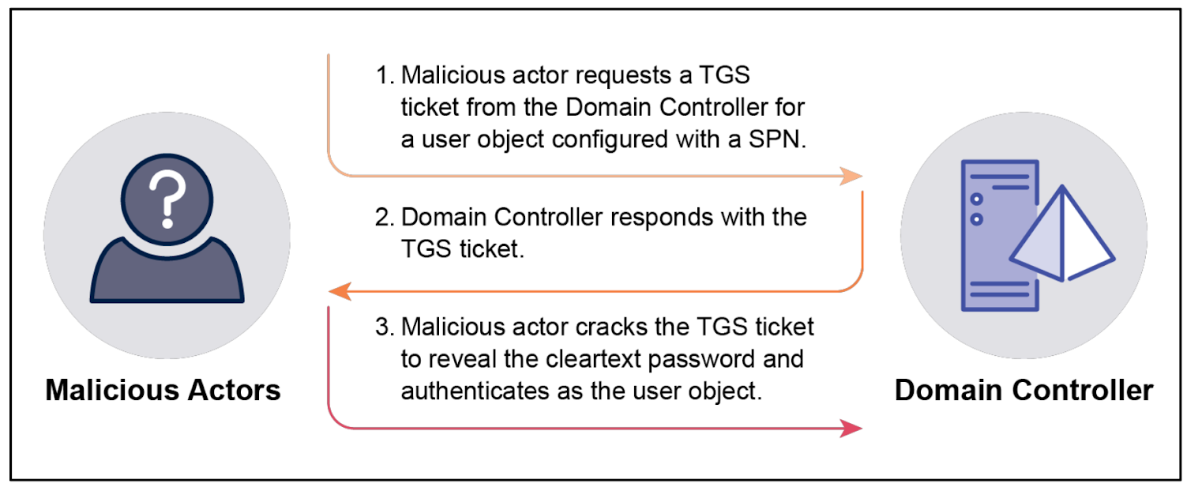
Figure 1: overview of Kerberoasting
Given the limitations of log and anomaly-based detection, detection engineering teams have tried to develop detections that specifically target evidence of particular offensive tools. However, attackers have adapted by using customized tooling, such as PowerShell variants of Mimikatz (e.g., Invoke-Mimikatz.ps1) and creating derivative tools like Kekeo to circumvent tool-specific detections. They are also increasingly using modern programming languages such as Rust and Go, expanding their arsenal with nearly infinite possibilities for custom offensive tooling. This adaptability means that a detection strategy solely reliant on identifying specific tools quickly becomes obsolete and ineffective.
Honeytokens: An Effective Approach to Detect AD Attacks
“The use canary objects in Active Directory is an effective technique to detect Active Directory compromises. The benefit of this technique is that it does not rely on correlating event logs, providing a strong indication a compromise has happened. Notably, this technique does not rely on detecting the tooling used by malicious actors (like some other detection techniques do) but instead detects the compromise itself. As such, it is more likely to accurately detect compromises against Active Directory.”
Defenders require a detection approach that is agnostic to the specific tools used in attacks and effective at uncovering stealthy AD threats. Honeytokens, or canary objects, serve this purpose well by detecting a broad spectrum of AD attacks.
By strategically placing honeytokens that simulate user and service accounts within AD, defenders can create proactive traps for attackers. The interaction with these deceptive accounts triggers immediate alerts, providing an early warning system and high-fidelity alerts that a compromise is underway.
This method of detection operates independently of the availability of log data or network traffic analysis. It is designed around providing controlled opportunities that align with an attacker’s objectives, such as elevating privileges, establishing persistence, or accessing sensitive data. By deploying honeytokens that appear as valuable targets—like administrative accounts for helpdesk or support services, or critical service accounts—defenders can lure attackers into revealing themselves. When attackers target these deceptive accounts, it triggers an alert, allowing for immediate defensive action.
Challenges of Manual Honeytoken Deployment
As honeytokens have become universally recognized and accepted as an effective strategy for enhancing Active Directory (AD) security, the demand for their deployment has increased. However, manual deployment of honeytokens presents significant challenges. It requires in-depth domain knowledge of both deception technology and the intricacies of AD attacks. For instance, creating a single user object in AD involves configuring over 100 attributes, requiring administrators to make numerous critical decisions to ensure each honeytoken is effective and believable. This complexity can lead to potential errors and oversights.
Given these difficulties, manual deployment methods are often inadequate for the efficient and effective placement of honeytokens. Instead, an automated approach is essential. Automation ensures that honeytokens are deployed systematically and consistently, reducing the likelihood of human error and significantly enhancing the speed and scalability of this defensive tactic.
Acalvio’s AI-Driven Innovations Enhance Honeytoken Deployment Easy and Effective
Acalvio’s platform revolutionizes honeytoken deployment through its automated, scalable, and AI-driven approach. The platform’s agentless architecture ensures that deployment does not impact Active Directory (AD) or production assets, maintaining system integrity. Additionally, Acalvio features native integrations with leading security platforms like CrowdStrike and Microsoft. This allows Security Operations Center (SOC) teams to monitor AD attacks directly from their existing consoles without altering their established workflows. The solution can also be deployed without requiring any software installation on-premises, providing immediate time to value.
The solution’s standout feature is its AI algorithms, which generate automated recommendations for creating realistic and compelling honeytokens specifically tailored for the AD environment. These honeytokens are designed to be particularly attractive to attackers, increasing the likelihood of early detection.
Acalvio’s technology is not only effective but also highly scalable. It supports automated deployment across hundreds of AD domains and can manage tens of thousands of endpoints with minimal administrative effort. This scalability ensures that organizations of any size can effectively enhance their AD security posture.
Acalvio honeytokens in action: example AD attack scenario (Kerberoasting)
Consider the case of an attacker attempting Kerberoasting attack. Acalvio deploys honeytoken accounts that are realistic and made attractive for attackers to exploit.
An attacker gains initial access to an environment and attempts to perform enumeration/reconnaissance using a custom offernsive tool, looking for a service account that is vulnerable to Kerberoasting.
The attacker finds such an account, performs the Kerberoasting attack, and attempts lateral movement with this account.
If the enterprise does not have solutions like Acalvio deployed, this attack would have gone undetected (as indicated in the Active Directory attacks section above), with the logs containing no actionable evidence and the custom tooling evading any tool-specific detection rules.
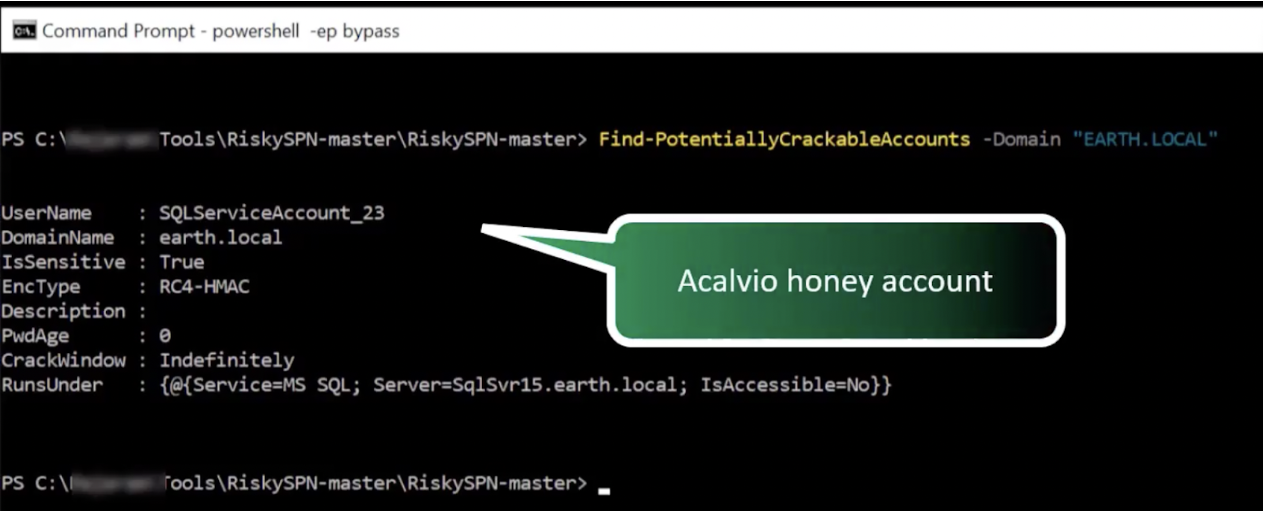
Figure 2: attacker enumeration surfaces Acalvio honeytoken accounts
This enterprise has Acalvio deployed and the account is an Acalvio honeytoken account. The lateral movement attempt results in an immediate alert to the defender and is followed by an automated response action, isolating the threat and stopping attacker propagation. This is an effective approach to detect such targeted attacks against AD, with no dependency on the presence of logs and is agnostic to the attacker tooling.
Conclusion: Regaining the Defender’s Advantage with Canary Detection Techniques
Attackers are targeting AD to elevate privileges and gain access to critical systems. The trusted access bypasses prevention-based security controls, increasing the need for a robust detection strategy. Traditional approaches to detect AD threats have proven to be insufficient, with attacker actions blending with normal activity, making it difficult to differentiate malicious activity from regular actions. As attackers continue to innovate and identify novel attack techniques and use custom offensive tooling, the complexity for the defender continues to escalate. By setting traps for the attacker in the form of honeytokens, defenders gain the benefit of an early warning systems that continues to remain effective as threats evolve. Defenders can regain their advantage and protect their critical assets from cyber attacks.
Explore Acalvio’s Advanced AD Security and Identity Protection Solutions
Interested in seeing how Acalvio can address the AD security challenges as outlined in the NSA guidance?
Download our ebook for more insights, or schedule a personalized demonstration of our platform’s capabilities.




