Ransomware demand in 2016 was around a billion dollars[1]. WannaCry[3] was the recent ransomware campaign that spread across 150 countries affecting 200,000 users. It is estimated that in 2017[2], damages due to ransomware will exceed $5 billion. Modern defenses make use of virtualized environments or machine learning algorithms to ensnare the threat actor. This blog will detail some of the evasion techniques that modern ransomware uses to bypass such defenses.
Virtualized Environment Detection: Inline detection solutions that monitor the web or email traffic, make use of virtualized environment for detonating of the incoming file. Once the file is dropped in the virtualized environment, its behavior is captured and is used to determine if the file is malicious or not. CryptoLuck, makes use of Windows API RegOpenKeyExA to open the registry keys and checks for the presence of VMWare, Virtualbox, etc. If any of these conditions are found, it is an obvious sign of a virtualized environment, the code exits, hiding its real behavior.
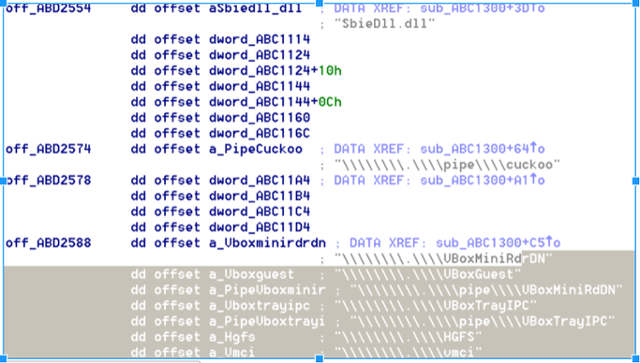
Techniques to detect the presence of virtualized environment have been used by other families of ransomware as well such as UIWIX. The ransomware checks for the presence of SbieDll.dll, which is one of the DLL used only by Sandboxie sandbox. It also checks if the execution environment is a cuckoo sandbox. If it detects the presence of Sandboxie or cuckoo sandbox, execution of ransomware terminates thus hiding its intended behavior.
- DLL Hijacking: When an application loads a DLL, the application searches for the DLL in the directory where it is executing. If the DLL is not found, then the application searches for the DLL in the windows system32 folder. In the case of DLL hijacking, the threat actor will place the malicious DLL in the same directory as the application. Since the application will first search for DLL, in the current directory, the malicious DLL will get loaded and executed. This technique can evade the detection algorithm which makes use of the host process for classifying the activity as malicious or benign. CryptoLuck ransomware uses legitimate application googleupdate.exe to load the malicious DLL with the ransomware payload.
- Password protected zip files: Detection architecture which monitors the emails, extracts the attachment from the emails and detonates them in the virtualized environment. If the attachments are passwords protected files, the file asks for password and will not get executed in a virtualized environment, and hence the actual behavior of the file is not revealed. One of the techniques to detonate the password protected files is to scan the body of the email for the password, and then enter the password. However, if the password and password protected files are in different emails, then it becomes a challenge to obtain the password and use it to detonate the file in a virtualized environment. Some ransomware leverage password protected Zip files to avoid execution in a virtualized environment. Bart family of ransomware[4] is one such example, which has used password protected zip files.
- Delivery Vector & File Formats: Threat actors have employed spam campaigns, downloaders and botnets, Malvertisement, exploit kits, etc. to distribute ransomware. The wide variety of delivery channels make it challenging for any organization looking to implement safeguarding approaches. In addition to email and the web, threat actors have used other more sophisticated approaches. Threat actors compromised an external-facing server, harvested the details from Active Directory and distributed the SAMSAM [5] ransomware to the compromised network. Psexec was then used to execute the ransomware. Today, an organization will need to monitor every delivery channel and back-door approaches. Each of these delivery vectors may require a different security architecture along with the algorithms to detect ransomware.
File Format Delivery Vector by Ransomware
Ransomware also used different file formats for delivering the malicious payload.
Conclusion:
Ransomware campaigns have employed techniques to evade the traditional security defenses making it an arms race. It is estimated that the total damages due to ransomware will reach around 5 Billion US dollars in 2017. In our upcoming blogs, we will detail the deception-centric solution to detect ransomware and its inherent advantages over traditional detection solutions.
References:
- Ransomware demand is a billion dollar crime and now growing, http://www.nbcnews.com/tech/security/ransomware-now-billion-dollar-year-crime-growing-n704646
- Ransomware damages rise to 15x to hit 5 billion in 2 years.
- Wann Cry Ransomware,
- Bart Ransomware Locks files in Password Protected ZIP files.
- SAMSAM Ransomware


