
Authors: Deepak Gujraniya, Mohammad Waseem, Balamurali AR, and Satnam Singh
Since the first attack in 1989 [1], ransomware attacks have gained popularity. Especially in 2017, it has created havoc in every possible industry, including the government offices, public-sector departments, and hospitals. Apart from the financial strain that ransomware can bring, it also affects everyday aspects of the public life. For instance, the WannaCry attack on hospitals, police stations, government offices have hindered daily life of the regular citizens of numerous countries [2]. To make the things worse, ransomware is now available as a service on the darknet. Any novice attacker can also avail the ransomware service to start their own attack. This leads to the situation in which same entity is attacked more than once.
Like other malware, ransomware also has a kill chain. That typically includes luring the victim via phishing or other means, loading the payload i.e. installing the ransomware on the target host, and finally spreading and detonating the ransomware i.e. encrypting the host’s memory and demanding for the ransom via a ransomware note. The ransomware attack starts when a user clicks a malicious web link or opens the attached file in a phishing email. Now, ransomware is installed on the target machine. Depending on the strain, the detonation can happen before it spreads. To encrypt machine’s data, ransomware need to use an encryption key. It may or may not use the Command and Control (C&C) to get the encryption keys. The ransomware without C&C use hardcoded encryption keys or locally generated keys and use the same keys for all the infected hosts. In this case, the security experts can reverse engineer the malware binaries and may find the keys. However, the ransomware using the C&C get the encryption keys from the C&C server hosted by the attacker. CryptoLocker, WannaCry, TeslaCrypt, Cerber, and Locky are some of the ransomware using the C&C that makes nearly impossible for the defenders to recover the encryption keys from the ransomware.
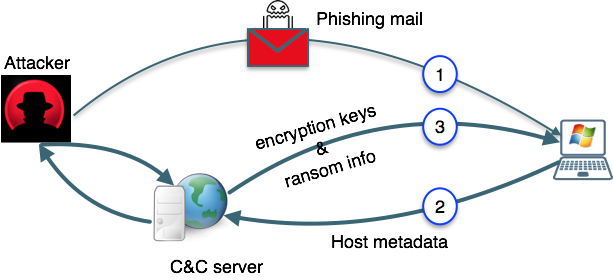 Figure 1: Ransomware attack using command & control (C&C) for encryption key management
Figure 1: Ransomware attack using command & control (C&C) for encryption key management
Ransomware use different asymmetric and symmetric encryption techniques e.g. RSA, AES for generating encryption keys. The attackers are becoming more sophisticated and using both techniques in combination. An AES key is hardcoded within the payload to encrypt the files on the infected machine and then an RSA public-private key pair is generated and used to encrypt the AES encryption key and the private RSA key is uploaded onto the C&C server.
In early variants of ransomware, the C&C server addresses were hardcoded in the malware binaries. It was easy for the defenders to find these addresses and block them. Once blocked, C&C servers could not spread the infection and encrypt files. To evade such security measures ransomware started using Domain Generation Algorithm (DGA)-based techniques to connect to C&C servers. With the DGA, attackers generate dynamic domain names and redirect their C&C servers to these dynamic addresses. Using DGA-based C&C the attackers can easily evade perimeter-based security defense tools such as firewalls, IDS/IPS, and even threat intelligence feeds.
The main use of the C&C is to contact the C&C server using a domain name, if the domain can be detected and blocked immediately, the attack can be stopped from spreading to other machines. For example, thisisyourchangeqq.com and gvludcvhcrjwmgq.in are two C&C domains that are used by TeslaCrypt and Locky ransomware respectively.
Ransomware connects to the C&C server using DNS queries. To establish the connection, DNS resolution queries are made for domains generated by the ransomware. These queries are captured in the DNS logs of the system. By analyzing DNS logs we can detect domains used for the C&C. In machine learning (ML), this problem can be posed as a classification problem where there are two classes i.e. benign DNS server and malicious C&C domain server. Several machine learning classifiers, such as Random Forest [3], Support Vector Machine (SVM) [4], Artificial Neural Networks etc. can be used as classifiers. Using discriminatory and informative features from the DNS logs, one can build a classification model to detect the C&C domains.
We trained a ML classifier using a Random Forest classifier to detect domains generated by DGAs. Features such as bigram and trigram scores are informative and discriminating to classify the C&C domains from benign domains. A bigram score tells how often that bigram is likely to occur in a normal english word [5]. This score is less in a DGA-generated domain. We computed trigram_benign and trigram_malicious scores that are fractions of trigrams present in the benign and malicious corpus respectively. The entropy of a domain is also different for both malicious and benign classes of domains. We used Shannon entropy [6] as another feature to differentiate between benign and malicious domains.
Example domain: google.co.in bigrams [‘$g’, ‘go’, ‘oo’, ‘og’, ‘gl’, ‘le’, ‘e$’, ‘$c’, ‘co’, ‘o$’, ‘$i’, ‘in’, ‘n$’] trigrams [‘$go’, ‘goo’, ‘oog’, ‘ogl’, ‘gle’, ‘le$’, ‘$co’, ‘co$’, ‘$in’, ‘in$’] Figure 2: An example of how bigrams and trigrams are extracted from a domain Below histograms shows how these features are discriminative for benign and malicious domains. Some features are more discriminative than others however all of them complement each other and improve the classification.
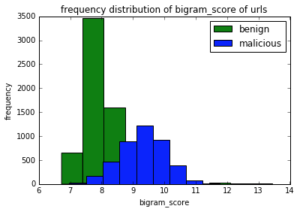
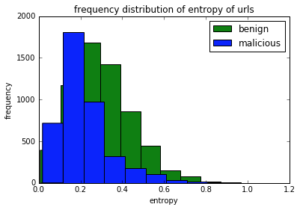
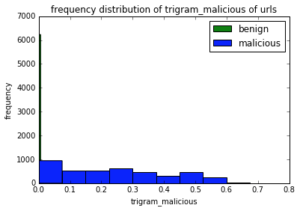
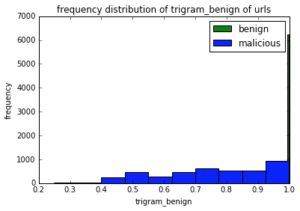
Figure 3: Frequency distribution plots of entropy, bigrams and trigram features
Example: Benign domains
| url | bigram_score | entropy | trigram_benign | trigram_malicious | class label |
| google.co.in | 7.28 | 0.44 | 1.0 | 0.0 | benign |
| bloomberg.com | 7.94 | 0.30 | 1.0 | 0.0 | benign |
| conservativetribune.com | 7.53 | 0.77 | 1.0 | 0.0 | benign |
| howstuffworks.com | 8.21 | 0.35 | 1.0 | 0.0 | benign |
Example: Malicious domains
| url | bigram_score | entropy | trigram_benign | trigram_malicious | class label |
| 52uo5k3t73ypjije.zzis8p.bid | 10.02 | 0.18 | 0.54 | 0.45 | malicious |
| equityaccountants.nl | 7.88 | 0.56 | 1.00 | 0.0 | malicious |
| 3qbyaoohkcqkzrz6.tordonator.li | 8.65 | 0.52 | 0.68 | 0.32 | malicious |
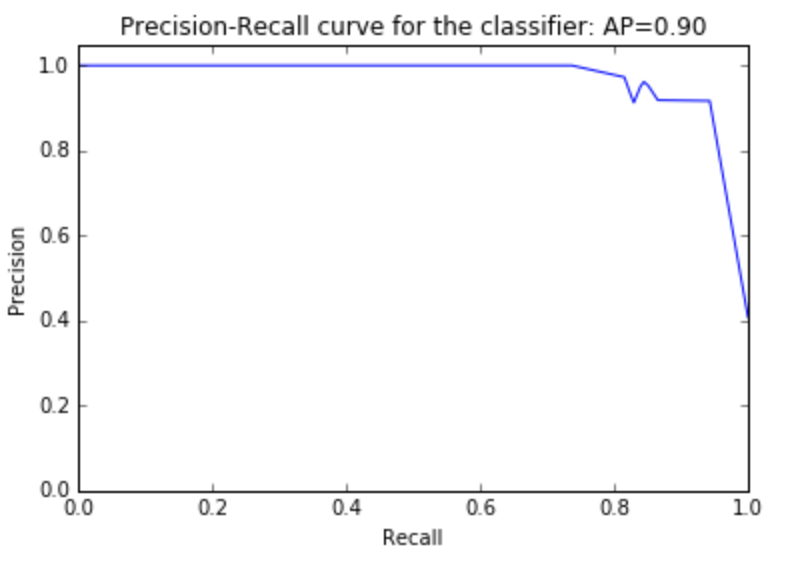
Figure 4: Precision-Recall curve for the classifier
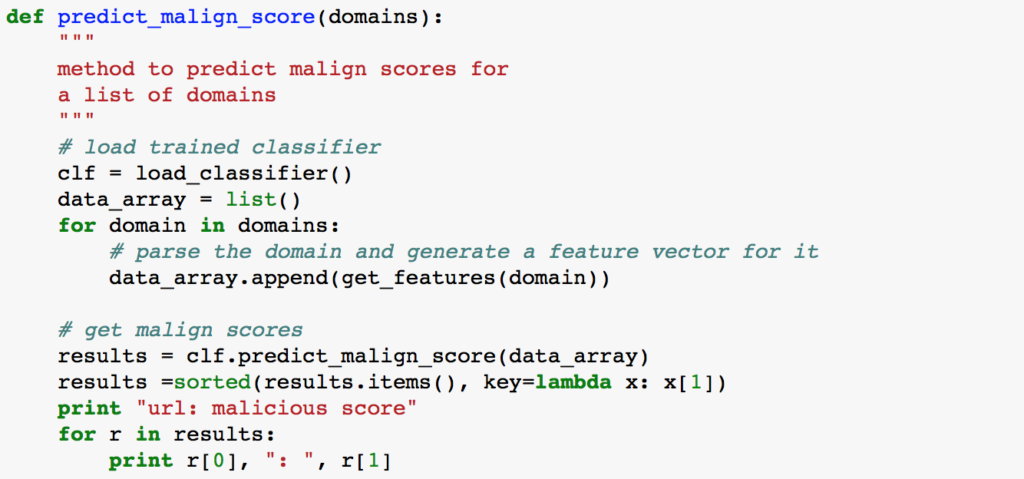
Figure 5: Code snippet of C&C Detection Classifier
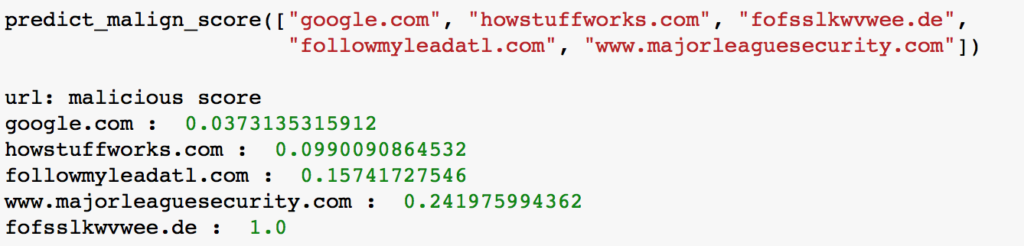

Figure 6: Test run on some normal domains and some C&C
In the above example, “google.com” and “howstuffworks.com” are benign domains and other domains are used by Locky [7] ransomware for the C&C. The domain “fofsslkwvwee.de” got the maximum malicious score (=1.0), however, other 3 malicious domains that look like normal domains got a score less than one. Typically, ML-based the C&C detection is deployed at the perimeter to monitor every DNS domain that needs big data infrastructure to process a high volume of DNS logs. Acalvio’s solution to the C&C detection is different and more effective than other solutions as our approach is event-driven instead of traditional boiling-the-ocean approach where every DNS query needs to be monitored. In our approach, we use deception to detect the ransomware and then leverage machine learning to detect the C&C. In this approach, one does not need to monitor all the DNS traffic all the time. Once detected, these domains can be blocked to stop spreading of the ransomware in the organization. We analyse the domains only when we detect ransomware attack from our deception-based solution ShadowPlex-R [8], hence the false positive detection rate is very low. 

Figure 7: Low False-Positive rate against various ransomware families
We tested our approach on nearly 20 different ransomware families and results are summarised in Figure 7. “Detected C&C domains” is the number of domains detected by our solution and “Actual C&C domains” was the actual number of the C&C domains used by the ransomware. Our solution can achieve nearly 100% true detection rate i.e. detect all the ransomware with a false positive rate of nearly 2.5%. The results demonstrate the power of combining deception along with machine learning for the C&C detection.
Conclusion:
Ransomware attacks are evolving at an unprecedented pace today and it is becoming impossible to detect them beforehand. In this blog, we explained how ransomware uses the C&C to encrypt the user data and how one can extract features from domains and train a ML classifier to detect the C&C domains. Many current techniques for detecting the C&C monitor logs continuously and inspect every domain request. This leads to a high number of false positives and is computationally expensive. With Acalvio’s deception-based solution ShadowPlex-R, we can detect a ransomware attack in real time and use a ML-based classifier to detect the C&C domains. A demonstration of ransomware attack and the C&C detection is available in our webinar [9] hosted by Acalvio and Splunk. References: [1]:Lord, Nord (2017, July 17), A history of ransomware attacks: the biggest and worst ransomware attacks of all time [2]: SANS whitepaper 2017 https://www.sans.org/reading-room/whitepapers/threats/sensitive-data-risk-2017-data-protection-survey-37950 [3]: Breiman, L., 2001. Random forests. Machine learning, 45(1), pp.5-32. [4]: Burges, C.J., 1998. A tutorial on support vector machines for pattern recognition. Data mining and knowledge discovery, 2(2), pp.121-167. [5]: Cheng Qi, Xiaojun Chen, Cui Xu, Jinqiao Shi, Peipeng Liu, A Bigram based Real Time DNS Tunnel Detection Approach, In Procedia Computer Science, Volume 17, 2013, Pages 852-860 [6]: Shannon, C.E., 1951. Prediction and entropy of printed English. Bell Labs Technical Journal, 30(1), pp.50-64. [7]: Locky. Wikipedia.,Retrieved November 19, 2017, from https://en.wikipedia.org/wiki/Locky [8]: ShadowPlex-r, Retrieved November 19, 2017, from /shadowplex-r/ [9]: Splunk webinar, Retrieved November 19, 2017, from https://www.splunk.com/blog/2017/08/18/webinar-learn-how-to-use-deception-to-defend-against-ransomware.html


