Modern adversaries are gaining in speed, with adversary breakout time down to an average of 62 minutes in 2024 compared to an average of 84 minutes in 2023. This poses a significant challenge for cyber defense.
Adversary breakout time is falling rapidly
Adversary gains initial access to an endpoint
Performs offensive actions (reconnaissance, credential access, privilege escalation, defense evasion followed by lateral movement)
Pivots toward a critical system
Adversaries propagate rapidly toward critical systems or sensitive data
Implications for cyber defense
Prevention based defenses are not sufficient
Adversary will always get to machine zero (initial beachhead)
A breach occurs when an adversary compromises critical assets or sensitive data. Stopping breaches is contingent on detecting threats before adversary breakout.
Traditional security solutions are unable to keep pace
Modern adversaries leverage existing utilities and credentials. This makes it harder to detect them using traditional techniques
Traditional detection mechanisms are based on observing and analysis
Requires a certain level of signal to emerge before classifying actions as malicious
Results in a longer detection window

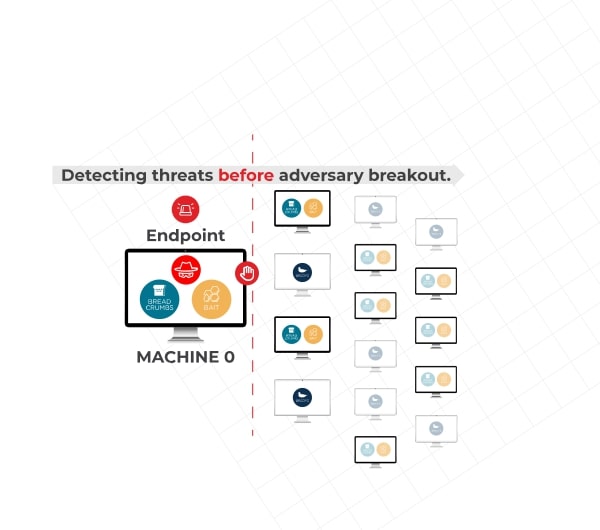
Deception provides early threat detection
Deploy deception at scale
Adversaries have two primary methods for propagation
- Credentials
- Vulnerability exploits
By setting relevant traps, the defense can detect adversary actions
Deceptions are not used in existing IT workflows
Any usage of a deception is indicative of malicious action
Provides instant threat detection
Set traps to detect threats early in the attack lifecycle (MITRE tactics)
Key criteria to achieve the goal
Deception should be deployed across the enterprise
- An adversary can gain initial access to any endpoint
- Deploying deception at scale is essential to detect threats early
Deception needs to be comprehensive
- Set relevant traps for adversaries
- Credentials, opportunities for lateral movement
Deception needs to be realistic, fresh, and dynamic
- Believable for the adversary
Accelerate your detection to stop breaches
Join forces with Acalvio to fortify your defenses and safeguard your digital future. Reach out today to learn more about our industry-leading deception platform and its role in early and precise threat detection to stop breaches