As traditional security perimeters dissolve with the advent of remote work and the proliferation of SaaS services, attackers increasingly exploit identities to infiltrate enterprise resources. With an alarming 80% of breaches involving compromised identities, the urgency for a robust defense mechanism has never been more critical.
Gaps in Traditional Identity Security
Despite having Identity Governance and Administration (IGA), Identity and Access Management (IAM) solutions in place, organizations remain vulnerable to identity-based attacks.

Policy-Based
Limitations
- IGA and IAM focus on policy enforcement and access control.
- They lack dynamic threat detection capabilities.

Evolving Threat
Landscape
- Attackers continuously develop new techniques
- They exploit gaps that policy-based solutions can’t anticipate or adapt to.

No Real-Time
Detection
- Traditional tools miss real-time threat
- Sophisticated attacks often slip through.

Adaptation Lag
- Traditional identity security tools struggle to keep pace, leaving exposure to novel attacks.
- Defense-in-depth is needed for multi-layers of protection.
Identity threat detection and response (ITDR) fills a critical need for identity-centric detection
Empowering Cybersecurity with Deception-based ITDR
Why Acalvio ITDR?
In an era where identities form the new battleground for cybersecurity, Acalvio presents a pioneering solution designed to fortify your digital defenses and secure the integrity of your identities.
Adversaries leverage stealthy identity offensive techniques that bypass traditional detection layers. Readily available penetration testing tools provide access to credentials, from identity caches on endpoints and identity stores. Deception technology is a proven approach for detecting current and evolving identity threats with precision and speed.
Fills a Critical Gap: Introduces a detection layer to eliminate the gaps from traditional layers, providing comprehensive visibility for identity threats
Advance Zero Trust maturity: Significantly advances Zero Trust maturity by protecting users/identities that are a foundational pillar of Zero Trust Architecture
Innovative Detection Mechanisms
Honey Accounts: Deceptive user and service accounts in identity stores like Active Directory, designed to attract and trap attackers.
Honeytokens: Deceptive credential profiles in identity caches on endpoints, providing early warning signals upon unauthorized use.
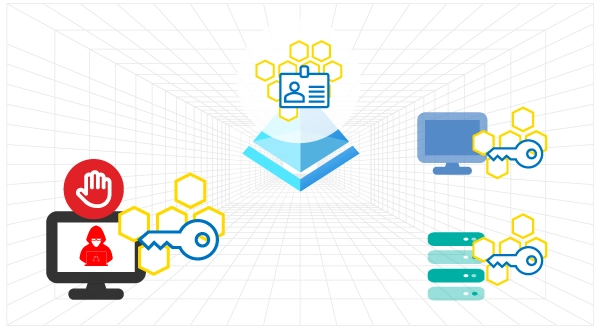
Comprehensive Identity Protection
Early detection of identity threats: Honeytokens detect identity threats before the adversary targets the identity infrastructure
Broad-Spectrum Defense: Equipped to detect stealthy and evolving identity threats that evade traditional security. Detect APT threat actors and modern ransomware that leverage identity-driven attacks
Ease of Deployment
Automated Configuration and Deployment: AI is used to automatically recommend, deploy and manage blended and targeted honey accounts across multiple domains and honeytokens across the distributed enterprise endpoints.
- Intelligent Deployment
- Seamless Integration
- Realistic and Attractive
Elevate Your Identity Security
Join forces with Acalvio to fortify your defenses and safeguard your digital future. Reach out today to learn more about our pioneering ITDR solution and its role in your journey towards a secure Zero Trust architecture.


