Red teaming simulates real-world adversarial actions. Organizations conduct periodic red team exercises to evaluate the effectiveness of their security controls. A failed red team exercise occurs when the red team is able to complete their mission without triggering alerts in the security controls. This raises concern and indicates gaps in threat detection. Security teams can deploy deceptions as a strategic countermeasure to eliminate the gaps and gain visibility for red team actions.
Red Team Exercises
- Periodic red team exercises simulate a real-world adversarial action
- They evaluate the readiness of the security controls to detect cyber threats
- Red teamers are skilled researchers with knowledge of offensive security
- They are typically given a goal or mission such as gaining control over a critical asset or a privileged identity
- The security team plays the role of a “blue” team, setting the defense strategy
- Organizations periodically conduct red team exercises to evaluate the effective of the security controls
Failed Red Team Exercises
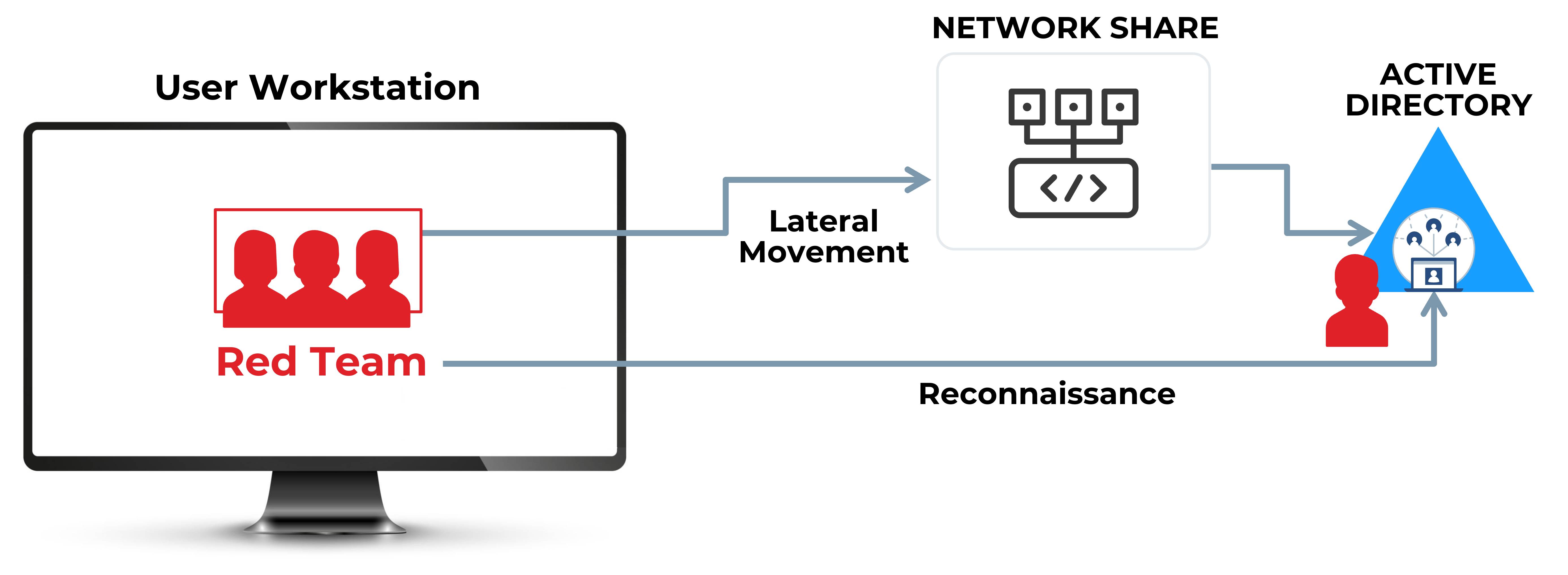
Red Team objective is to become the Domain Administrator

If the Red Team gets to the Active Directory without an alert, then it is considered a Failed Red Team Exercise
Red teams have multiple stealthy techniques to evade traditional security solutions and accomplish their mission without getting detected:
Living Off the Land (LOtL)
Cached Credentials
Defense Evasion
Catalog Reconnaissance
Failed red team exercises are indicative of lack of sufficient preparation to defend against a real attack
- Occur when the red team achieves their objective without raising alerts
- Indicates detection gaps and weaknesses in the security controls of the enterprise
- A real adversary could exploit the detection gaps, resulting in a breach
- Security teams need to strengthen the defenses as a countermeasure
Security Teams Can Deploy Deception as an Effective Countermeasure
- Security teams need a detection approach to eliminate the gaps exploited by the red team
- Deception technology provides an effective countermeasure
- Deceptions are placed strategically on all attack pathways
- Introduces uncertainty for the red team
- A single misstep by the red team results in an immediate detection
- Security teams can deploy a carefully tailored deception strategy
- Strengthens the security posture and readiness for a real cyber threat
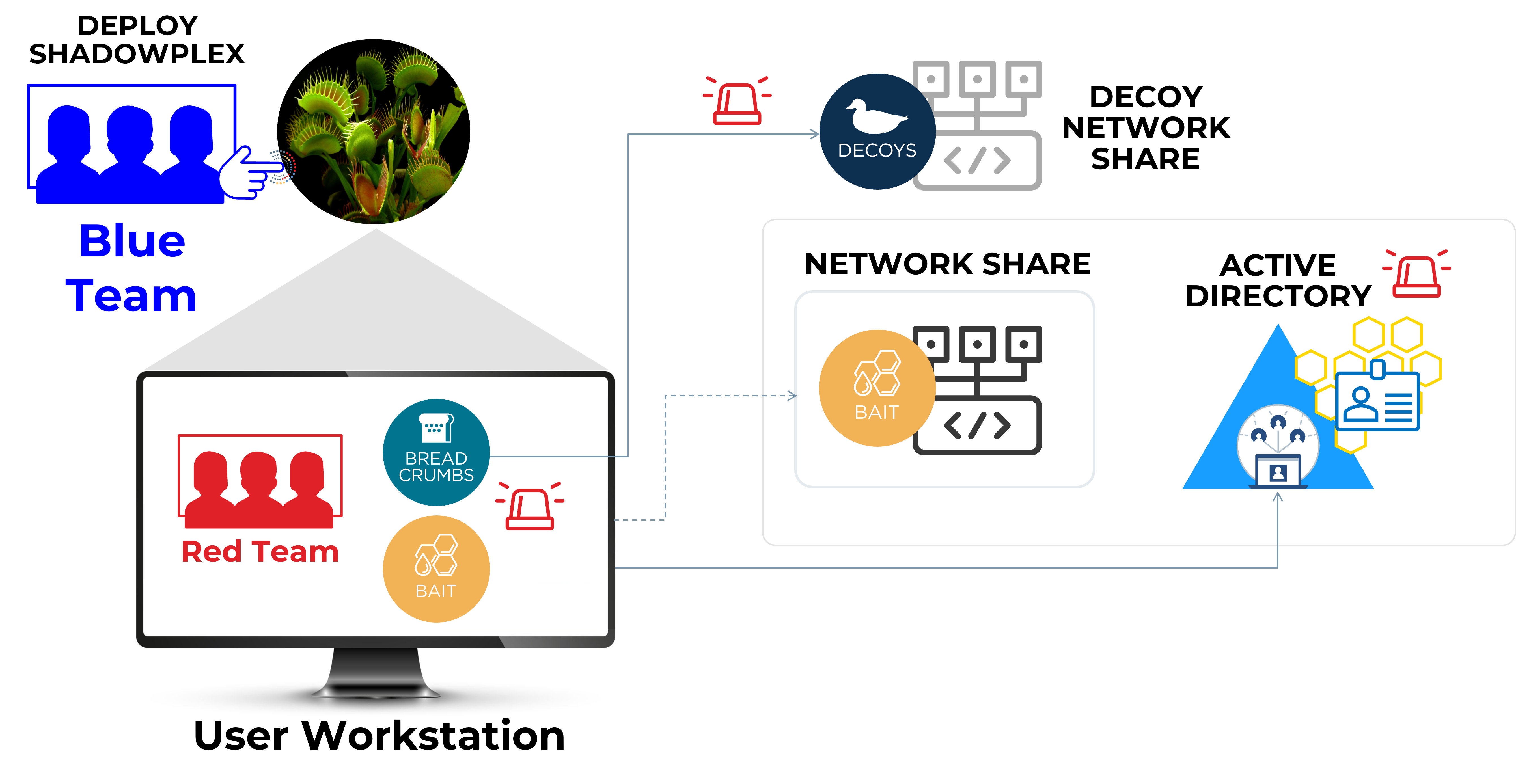
Blue Team deploys deceptions on assets and attack pathways
Deceptions lead the attackers to decoy networks and endpoints, triggering alerts and allowing administrators to block the attack and trap the intruder
Proven Efficacy Against Red Teams
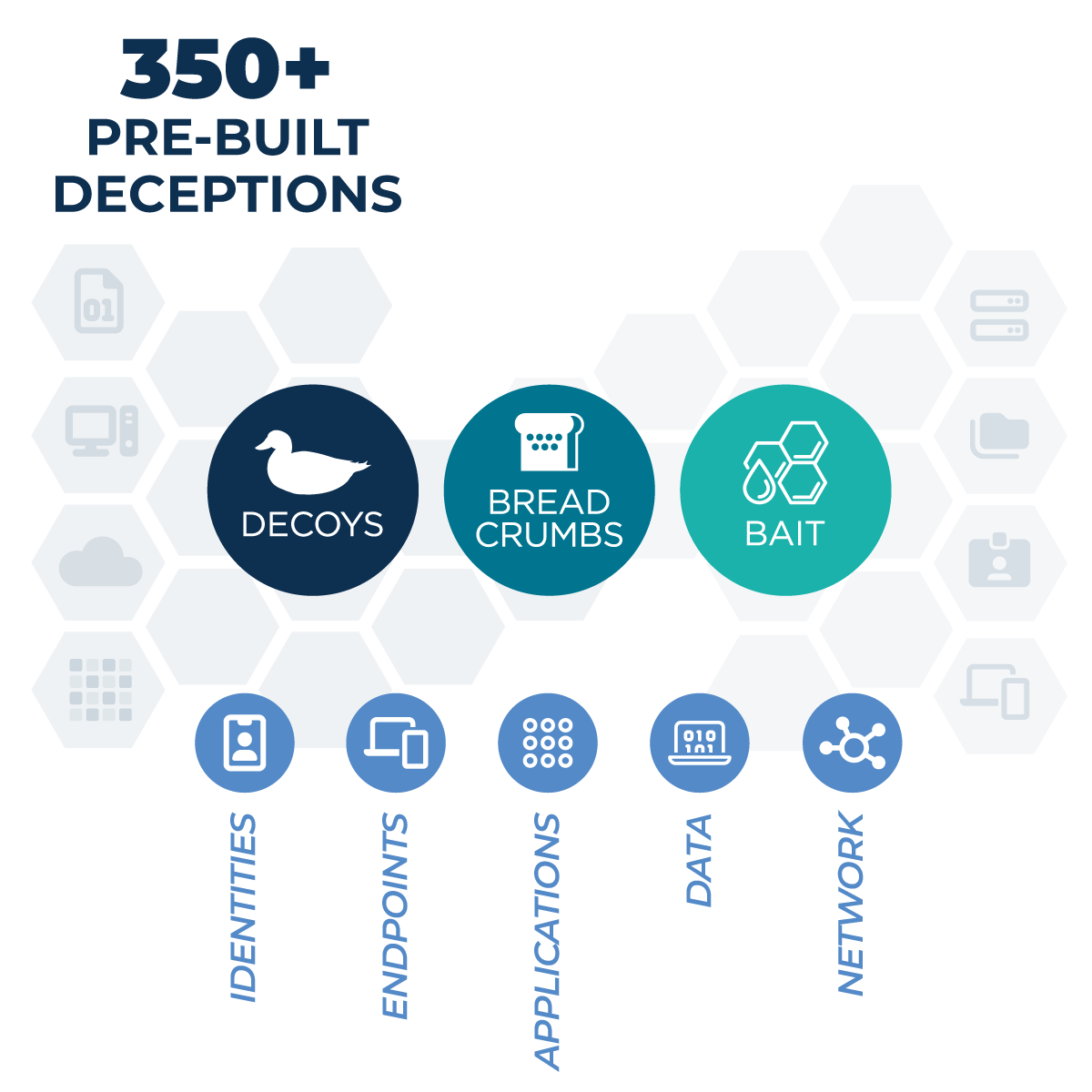
- ShadowPlex provides an extensive palette of prebuilt deceptions to represent assets in the environment
- Decoys are adjacent to the real assets and create alternate pathways and targets for the red teams
- Baits and honeytokens are deployed on endpoints to detect red team actions on the endpoint
- Detect multiple MITRE ATT&CK tactics
- Deceptions serve as primary detection of a subsequent red team exercise
- For purple team exercises, ShadowPlex deceptions can be deployed in real time, during the exercise
Using ShadowPlex pre-built deceptions, the Blue Team detected the Red Team every time!
Enhanced Detection Capabilities
Eliminate gaps in traditional security
Improved Response Time
High fidelity alerts enable blue teams to act rapidly
Strengthen Security Posture
Improve preparation for a real-world attack
Strategic Advantage
Detect future red team actions without need for tuning
Slow Down and Divert Attacks
Introduce uncertainty for red teams
Proactive Defense
Security team sets a strategy based on the objectives of the red team
Comprehensive Threat Intelligence
Gain visibility to attack TTPs
Continuous Improvement
Dynamic deception deployment for purple team exercises