Threat hunting is a proactive approach to cybersecurity, to identify the presence of malicious activity. Threat hunting typically starts with a hypothesis and involves a series of iterative steps to confirm the hypothesis. Traditional forms of threat hunting are based on log/event searches and IoC sweeps. While useful, these can be time consuming and error prone. Defense teams need an active approach to threat hunting, that brings precision into this activity.
Traditional Threat Hunting Approaches
Are Time Consuming and Resource Intensive
- Threat hunting actions have been based on searches in logs/events and IoC sweeps
- Adversaries can evade IoC sweeps through custom tooling and offensive TTPs
- Log volume can be voluminous, making the searches time-consuming and laborious

Defense teams need new approaches that bring precision
and an “active” element to threat hunting
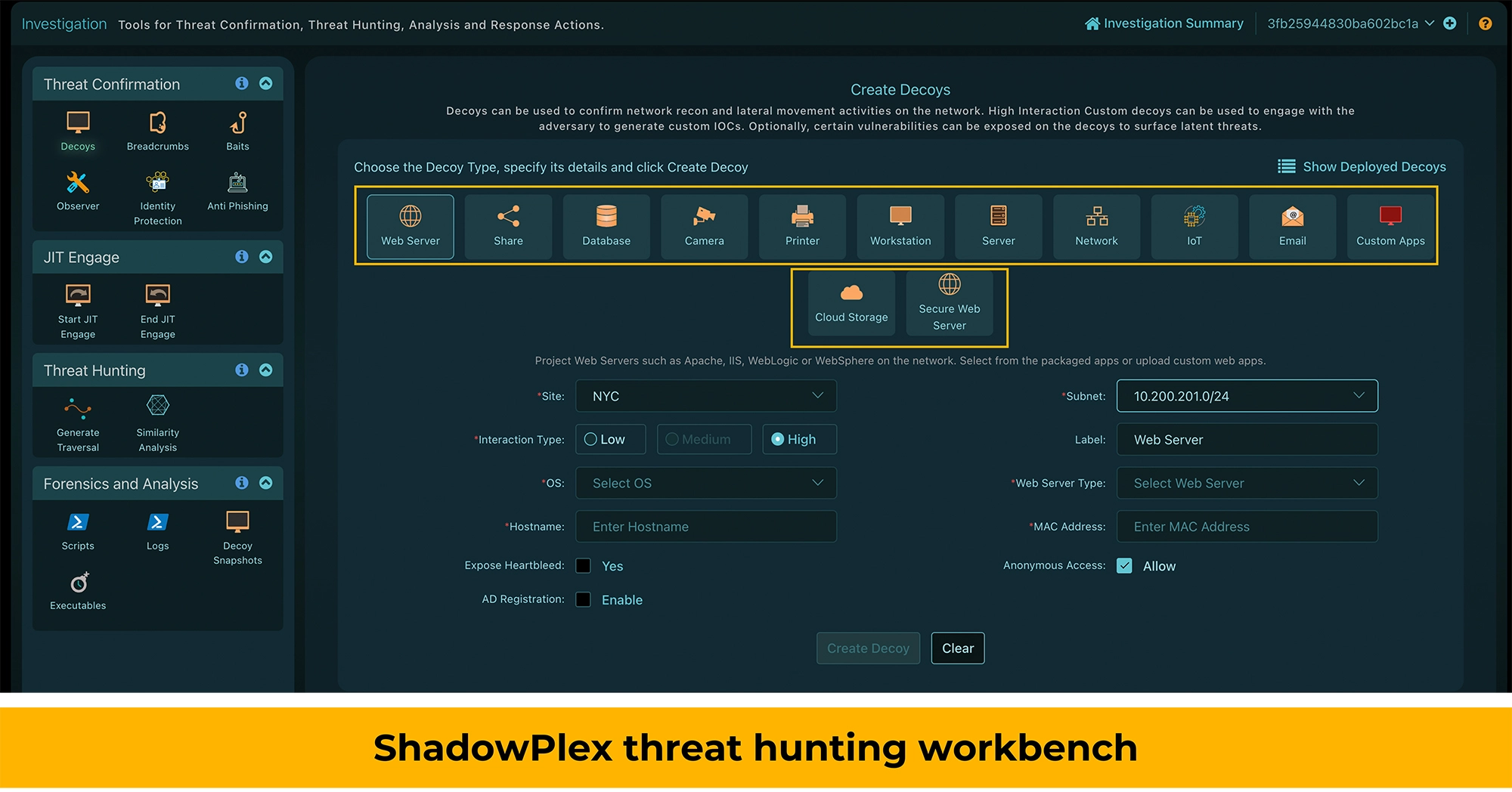
Acalvio Brings Novel Deception-based Threat Hunting Capabilities
- Acalvio provides a dedicated threat hunting workbench with deceptions
- Deploy deceptions to provide a controlled opportunity for latent threats to surface
- Confirm hypothesis to bring an active element to threat hunting
Adversary Traversal
- AI-driven automated analysis leverages a known security incident and uses data from the enterprise data lake to trace the path of the attack through the enterprise network
- Narrows down the set of potential compromised assets and enables rapid investigation
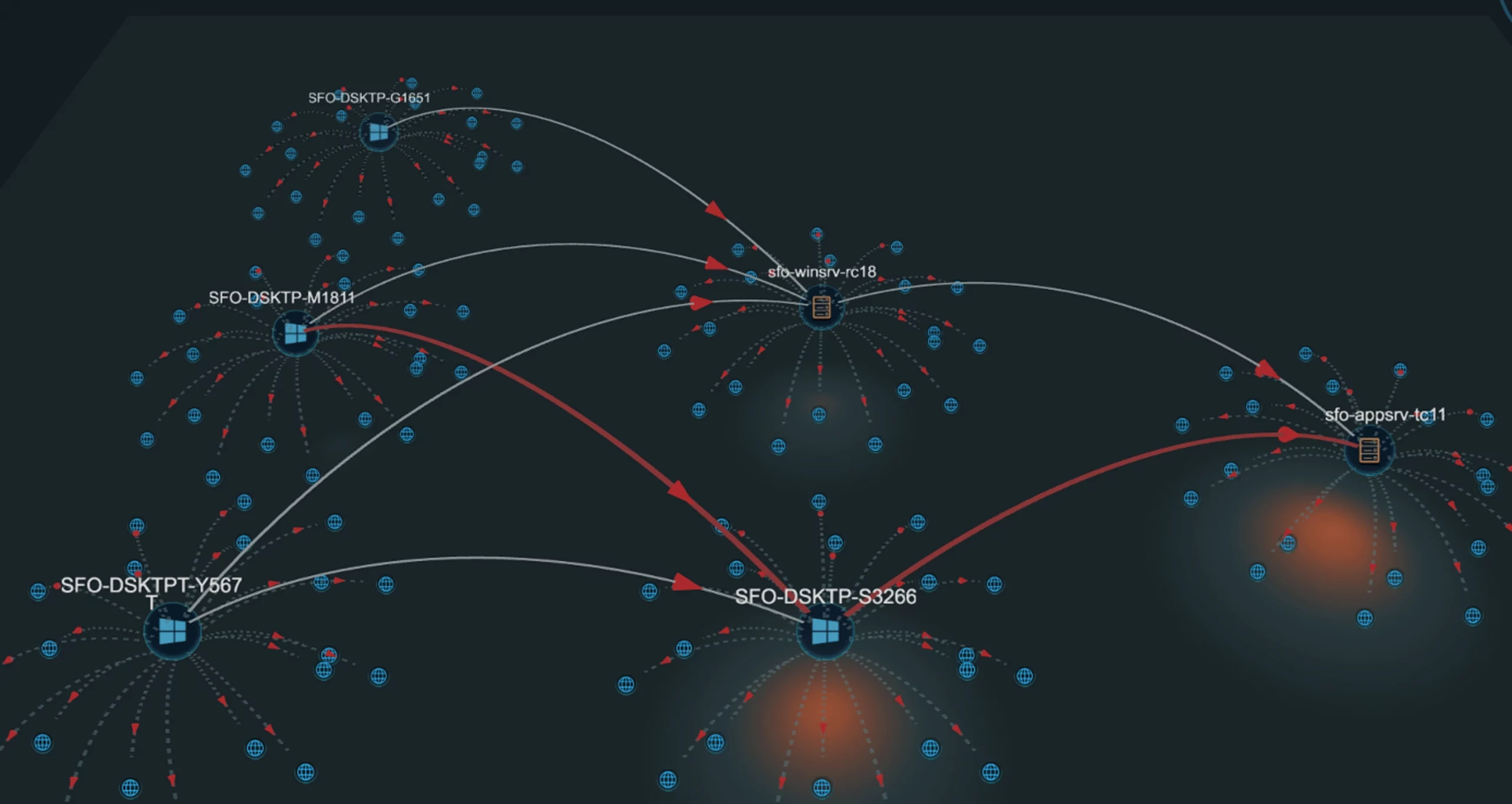

Similarity Analysis
- Innovative AI-driven automated analysis leverages data collected from known compromised machines to determine the list of similar exploitable enterprise assets
- Extracts additional value from existing enterprise data lakes
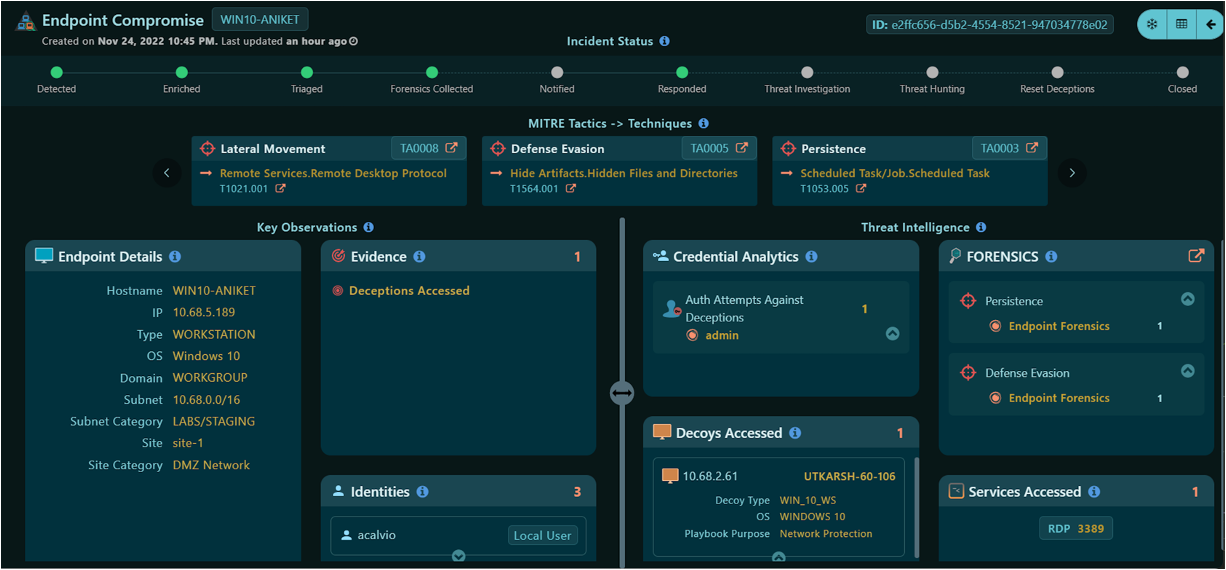
Endpoint Forensics
- Deep and comprehensive forensics collected on any compromised enterprise endpoint
- AI-Driven analysis to determine attack TTPs
- Increases SOC efficiency by making compromised endpoint analysis faster and easier
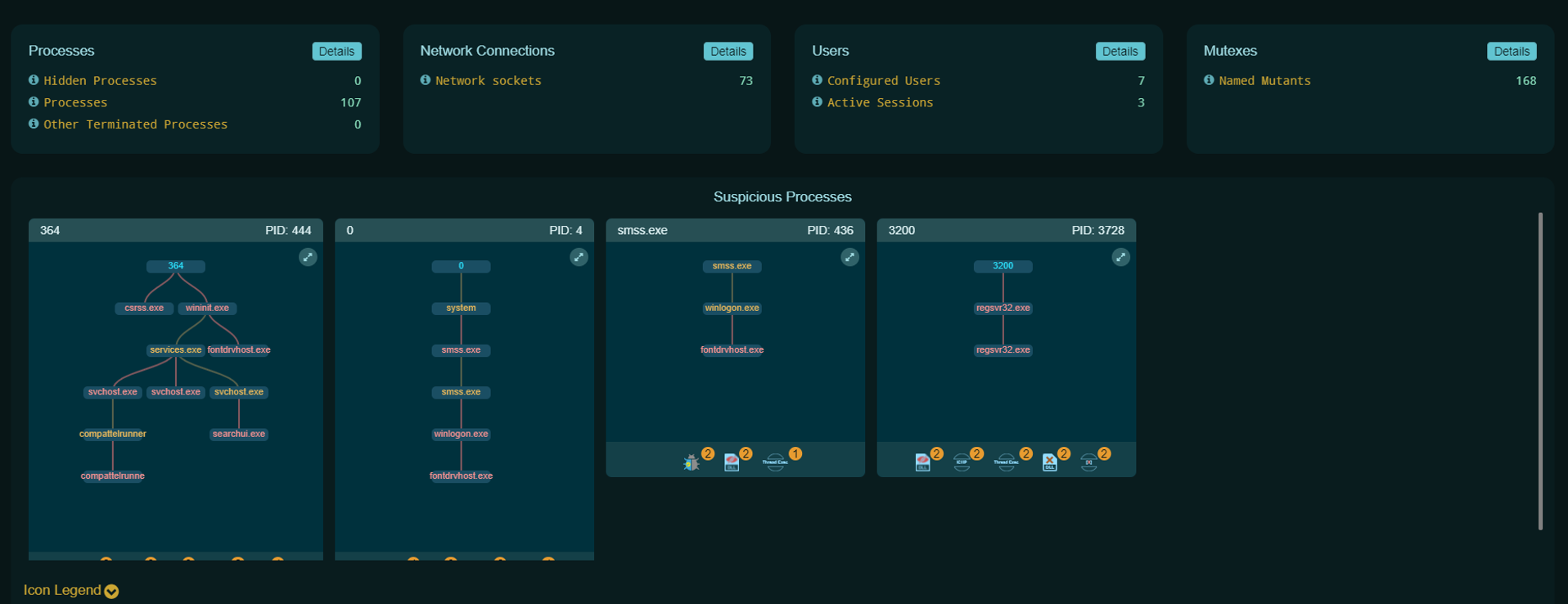
Memory Forensics
- Visibility to in-memory exploits
- Identify stealthy techniques such as Process Hollowing
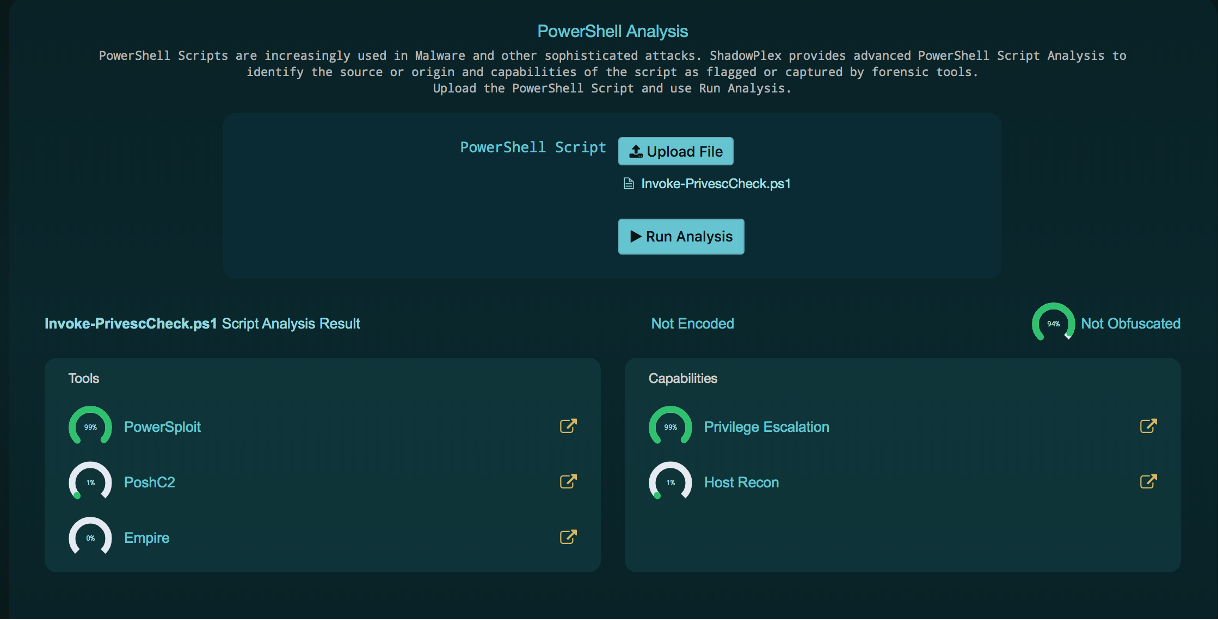
PowerShell Script Analysis
- Identify origin and capability of malicious script
- Understand adversary background/intent

Link Analysis
- Link various security events for a holistic view
- Highlights the relationship across deception events and endpoint events
- Shows attack progression
- Provides situational awareness
Discover More
Learn how Acalvio enables active threat hunting.
Gain a novel approach to threat hunting
Join forces with Acalvio to gain an active dimension to threat hunting, deploying deceptions for hypothesis confirmation and analytics for precision visibility to attacker TTPs


